Infrastructure Shortfalls Impact Security
As the past few weeks have shown, IT priorities and overall business focus have changed dramatically. Many enterprises are now faced with tough choices. It is not a question of which new applications or technologies to implement. Rather it is one of making sure the infrastructure
of IT is not bloated and can deliver world class service in a cost effective manner.
If any monies are spent they must be to meet mandated requirements or improve the productivity of the enterprise. It goes without saying there will be fewer resources available in the near term and only those IT organizations and mangers who can adapt to the new realities will succeed.
- Fully indexed electronic book (600 pages) in PDF format which can be place on your enterprise's internal network
- Each job description comes as an Individual Word files {Word format)
- PDF book and Word files
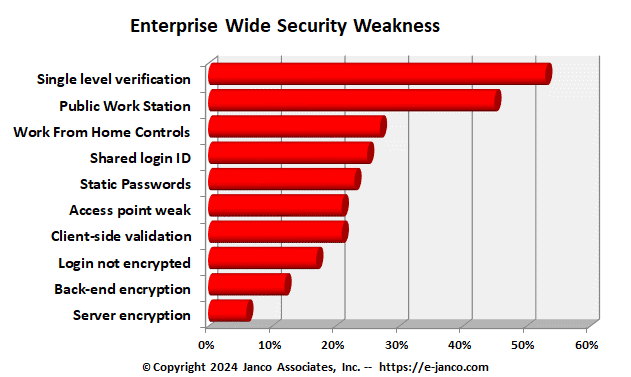
Everyone talks about security, but there continue to be an ever increasing number of security and data breaches that occur. Janco has reviewed over 100 instances of security and data breaches and found a number of core factors why these continue to occur.
- Data volumes and velocity of change are increasing at an exponential rate - In many enterprises data is dispersed, disorganized, and so voluminous that classifying it comprehensively and implementing standard security standards is resource-intense and one that most IT departments are not staffed to do.
- Information Technology (IT) Departments are reactive not proactive - IT departments are reluctant to invest their increasingly stretched resources in deploying another complex enterprise level infrastructure at the expense of delivering strategic value to the organization. IT departments that fail tend to respond to problems after the fact versus identifying solutions before a problem occurs.
- User do not want to change or add processes - there is a wariness about deploying yet another set of rules and tasks to follow on each Smartphone, desktop, and laptop that might interfere with doing the users job by adding procedures, hogging processor cycles, requiring frequent updates, and slowing down the user as they try to do their jobs.
- Complexity of security compliance - devising and implementing a comprehensive, viable security policy may get in the way of traditional business practices, requiring the involvement of not just IT but also human resources, finance and legal teams, and business unit managers.
- Addressing 20% of the problem versus the 80% - many enterprises focus on intentional data leakage, when in reality most data leakage occurs when there is a lapse and simple proactive steps like enciphering sensitive files on laptops and seeing that only those individuals that need sensitive information have it could have prevented the problem in the first place.
Order Security Security Audit Program Download Selected Pages

Users Demand 24 x 7 Availability
Users demand 24 x 7 IT service availability via web sites, portals, email, and mission critical applications. When these systems and applications are not there or are operating in a degraded mode, it negatively impacts the reputation and revenue of an enterprise. Maintaining availability and preventing downtime begins with the successful deployment of network and system management solutions that are focused on IT Service Management in a Service-Oriented architecture.
When managing the help/service desk in an IT Service Management environment (ITSM) with Service-Oriented Architecture (SOA), there are four (4) things that you need to do. They are:
- Validate that you have implemented service tools versus having added unnecessary overhead and bureaucracy. Evaluate your policies, procedures, and processes from the user perspective. To be a service desk, you must serve your clients, rather than make them change what they do to meet your needs.
- Survey your users often and understand what they do not like Review the comments and listen to critics with an eye improving what you are doing. When a change is implemented go back to the critics and see if you have improved.
- Implement metrics and track performance over time Use metrics that apply to your users, see what the trends are overtime. In addition, use the same metrics to see how your competition is doing. Determine if you are providing world class service or just average service.
- Determine the cost of a service solution and its ROI before you implement it measure achievement. Be professional in implementing changes to your help/service desk. If you are constantly changing the process you will not know if your changes are having the right impact.
- Encourage input from your users Listen to your users, validate that the problem that you are solving is the one the user want solved. Listen to your clients. Tell them what you heard them tell you and what your action steps will be. After you implement the solution confirm with them what you did and how it worked.
Read On Order Download TOC ITSM
